As a leading healthcare group, information forms a cornerstone and enabler of our worldwide business. Ongoing digitization and digital transformation provide great opportunities for health care – with innovative, technological, and medical approaches that improve the overall patient journey and treatment. Fresenius is continuously digitizing its processes and entering new markets with digital product solutions while acknowledging that digitization are associated with cyber risks. Our stakeholders have a high level of trust into the cybersecurity of our products and services. We continuously strive to meet their expectations by strengthening our resilience towards cyberattacks, and continuously reducing our cyber risks with the sole objective of preventing harm to our patients, customers or the company.
Our approach
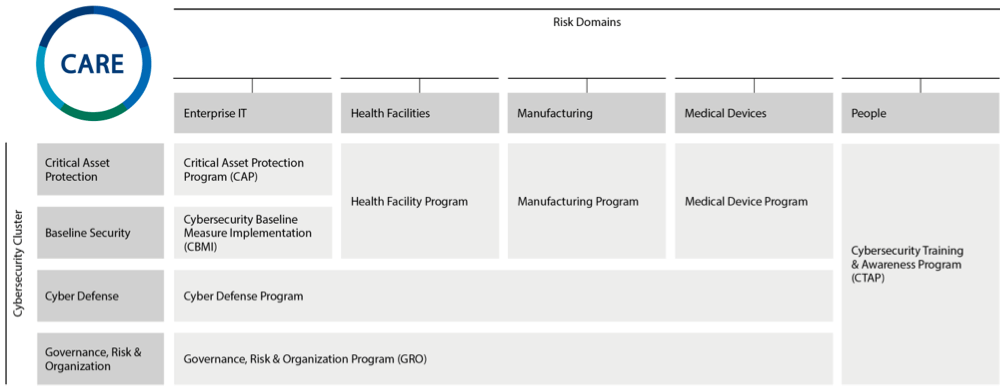
At the Fresenius Group, we pursue a holistic approach to the management of cybersecurity. We bring cybersecurity and business decision-makers in the Group together to execute a joint approach aligned with our strategic objectives. The core of our approach is to determine the right level of protection that balances the value of cybersecurity with the needs of the business as well as the cost of protection. We derive our activities based on maturity assessments and cyber-risk analyses that help us prioritize the most relevant measures to buy-down risk and carefully track both the progress as well as the effectiveness of implemented measures through our CARE program (Cybersecurity Approach, Roadmap and Execution).
The steering committee of the CARE program formally enacted the CARE Governance Charter to emphasize the strategic objectives, the scope and the responsibilities of the CARE program and the CARE Steering Committee as a governance body, as well as responsible function for escalation and decision processes. The CARE program is structured across risk domains (for more information refer to the Security concept section) and cybersecurity clusters to ensure a holistic consideration of our digital environment:
- Critical Assets Protection: measures to identify and adequately protect information assets that are considered critical to Fresenius business processes.
- Baseline Security: measures to provide an adequate cybersecurity baseline to protect all information assets based on minimum cybersecurity standards.
- Cyber Defense: measures to improve the capabilities to effectively detect and respond to cybersecurity incidents and reduce adverse impacts on our business.
- Governance, Risk & Organization: measures to improve the governance, the transparency of risks and the development of an adequate, efficient, and effective cybersecurity organization.
The Management Board of Fresenius Management SE initiated CARE. CARE bundles cybersecurity initiatives to strengthen our resilience in preventing and defending against cyberattacks. In 2020, the Management Board enacted a Group-wide Cybersecurity Policy that defines the objectives, structure, and operational organization for cybersecurity governance across the Fresenius Group, embedded in CARE.
CARE program
The Opportunities and Risk Report contains further information on cybersecurity at Fresenius in 2022, in the Risk areas section.
Organization and responsibilities
The Chief Financial Officer (CFO) of the Fresenius Group Management Board oversees cybersecurity governance and receives direct reporting from the Group Head of Cybersecurity. The position of the Group Head of Cybersecurity, who acts as Group-wide Chief Information Security Officer (CISO), has overall responsibility for the governance of cybersecurity within the Fresenius Group and leads the Group Cybersecurity Office (GCSO). He defines the Group-wide cybersecurity strategy and coordinates this strategy with the respective cybersecurity heads in order to ensure a consistent approach across all business segments. The CFO of the Fresenius Group is informed about cybersecurity-related topics on a weekly basis, or as required, by the Group Head of Cybersecurity. The Group Head of Cybersecurity reports quarterly to the Management Board of Fresenius Management SE and at least annually to the Supervisory Board.
In the four business segments, the respective Business Segment Heads of Cybersecurity (Segment CISO) are responsible for all cybersecurity matters. At Fresenius SE & Co. KGaA level, the Corporate Head of Cybersecurity is responsible for the individual corporate functions.
The GCSO enables and governs cybersecurity across the Fresenius Group. It ensures that cybersecurity is considered holistically and coordinated from a Group perspective, defines the baseline, and monitors its compliance as well as the execution of risk treatment plans. Where necessary, the business segments are advised and supported in their activities.
Cybersecurity Organization
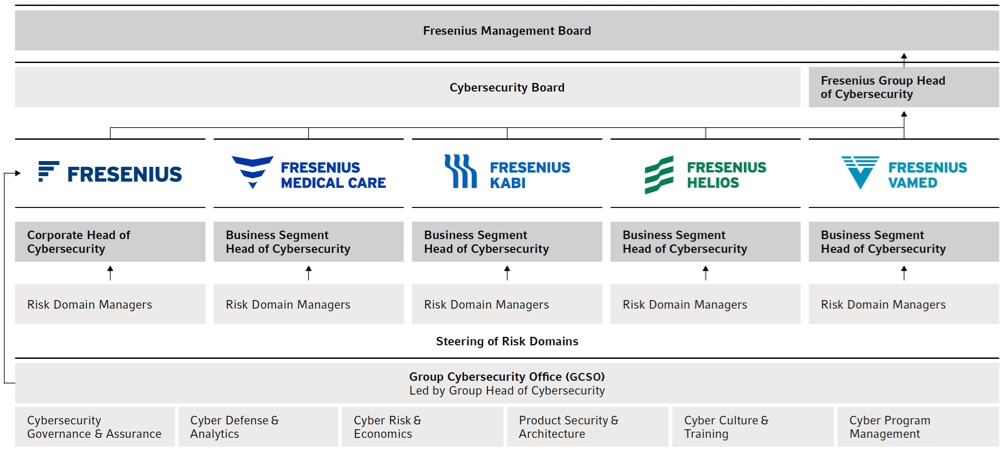
The GCSO is composed of six functions:
- Cyber Governance & Assurance,
- Cyber Defense & Analytics,
- Cyber Risk & Economics,
- Product Security & Architecture,
- Cyber Culture & Training, and
- Cyber Program Management.
At the operational level, the four business segments are responsible for their cybersecurity management. The Management Boards and managements of the business segments establish and report on strategic objectives and strategies for addressing risks. The objectives are based on the Group-wide cybersecurity strategy and are defined by the Business Segment Heads of Cybersecurity, who are responsible for implementation.
Within the Group, overarching committees have been established to complement the existing organizational structure. The cross-divisional Cybersecurity Board meets on a monthly basis. It consists of the Group Head of Cybersecurity, the Corporate Head of Cybersecurity, and all Business Segment Heads of Cybersecurity. It ensures the exchange of information on Group-wide cybersecurity matters between the business segments and Group functions, defines criteria for evaluating and monitoring the development of cybersecurity across the Group, and reviews the progress and results of cybersecurity measures and initiatives. The Cybersecurity Board also monitors the adoption and implementation of the Group-wide cybersecurity policies, baseline compliance and risk treatment plans.
The individuals responsible for cybersecurity usually have many years of experience in cybersecurity management, extensive knowledge, and appropriate professional certifications.
The CFOs of the business segments, and for Fresenius Vamed the member of the Management Board responsible for the service business, form the CARE Steering Committee which meets quarterly to organize regular reporting as well as to steer the cybersecurity initiatives across the business segments.
The Business Segment Heads of Cybersecurity inform the respective members of the CARE Steering Committee and additionally report on cybersecurity matters to their segment Management Boards at least on a bi-annual basis.
The Risk Domain Managers report to their respective Heads of Cybersecurity. In addition, the Risk & Integrity and Internal Audit departments regularly exchange information on matters relating to cybersecurity.
Guidelines and regulations
Our Cybersecurity Policy Framework consists of a set of policies, requirements, and procedures. It forms the foundation for cybersecurity in all business segments and Group functions. Within this framework, we define confidentiality, integrity, and availability as our key objectives for protecting digital information, technologies, and systems across our risk domains.
Cybersecurity policy framework
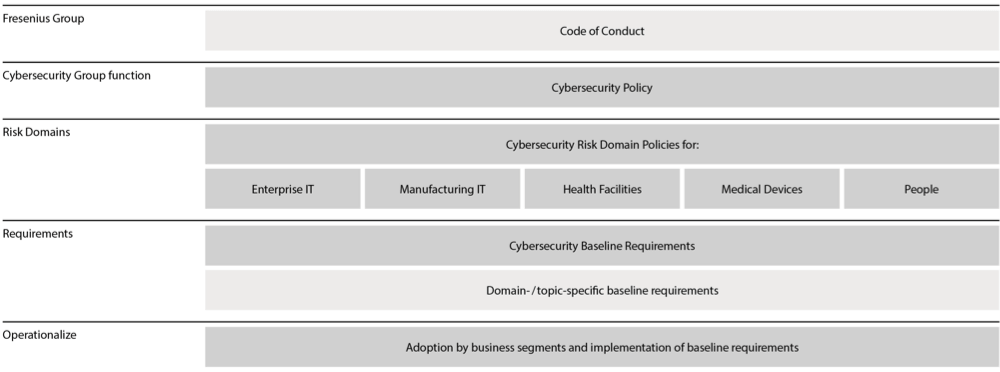
The Group Cybersecurity Policy is based on the Fresenius Code of Conduct and follows internationally recognized standards and best practices, such as the Charter of Trust. It defines the overarching policy and organizational structure for cybersecurity governance in the Fresenius Group. The underlying Risk Domain Policies specify the framework, processes, and roles and responsibilities for each risk domain to attain the overarching objectives of protecting the confidentiality, integrity, and availability of Fresenius’ digital information in a holistic manner.
The four business segments also have specific security standards, which take into account specific regulatory requirements and local legislations. Security standards already established in the four business segments are leveraged as Group-wide standards where appropriate.
Certifications and commitment
Cybersecurity insurance policies are in place at business segment level, where available in the insurance market and deemed suitable for risk transfer. In addition, there are certifications such as ISO / IEC 27001 at Group and business segment level. In addition, to complement the governance structure for risk mitigation and to further hedge risks, the conclusion of global cybersecurity insurance will continue to be evaluated at Group level.
Risk analysis
In accordance with the Group-wide Cybersecurity Risk Management Framework, the business segments – together with the GCSO, if required – conduct a business-driven evaluation of the strategic cybersecurity risks along Fresenius’ value chains. The cyber risks of the Group are attributed to the business activities of the respective business segments. While the cyber risks in the product business are closely related to interruptions to manufacturing or logistic processes, as well as theft of intellectual property, the risks in our healthcare facilities are related to patients, their health information, and the medical devices used. We continuously analyze the evolving cyber threat landscape to consider arising threats in our bi-annual cyber risk assessments in order to derive our cybersecurity measures and effectively mitigate our risks.
Our Risk Report contains extensive information on the effects of cyber risks on risk management; see the Risk areas section of our Annual Report 2022.
Security concept
To manage Group-wide cybersecurity and associated risks, we have determined five risk domains. These are managed by the respective Risk Domain Managers at corporate level and in the four business segments. Facilitated by the GCSO, the Risk Domain Managers form Special Interest Groups (SIGs) that define tailored cybersecurity requirements and coordinate risk management activities based on applicable best practices. They exchange of expertise and knowledge throughout all cybersecurity areas across the Group.
The five Risk Domains are:
- People: refers to the human factor of cybersecurity and includes all risks that could negatively affect the confidentiality, integrity, and availability of digital information due to inappropriate human behavior.
- Health Facilities: refers to cybersecurity in all health facilities such as hospitals, clinics, and treatment and rehabilitation centers. Related cyber risks include all risks that negatively affect the ability to serve patients.
- Medical Devices: refers to the cybersecurity of medical devices during their entire life cycle, from design to decommissioning. The risk domain includes all risks that could negatively affect the functionality and usability of medical devices.
- Enterprise IT: refers to cybersecurity in offices and administrative environments. This risk domain includes all risks that could negatively affect the ability of the cybersecurity of IT services to manage and process digital information.
- Manufacturing IT: refers to cybersecurity for production environments and associated facilities such as laboratories and warehouses. Related cybersecurity risks could negatively affect the performance and quality of production, including the ability to produce, label, and distribute products and meet compliance criteria.
To protect the Group’s value generation, we have developed tailored frameworks for our five cybersecurity risk domains that define the security architectures, concepts, and requirements. The respective preventive, detective, and corrective measures are prioritized and implemented through our CARE program to effectively mitigate risk. While our main objective is to prevent cyber risks from materializing, our investments into the early detection of cyber threats are paying off. We detect cyber threats at an early stage in what is known as the cyber kill chain through various monitoring solutions and are able to respond in a timely manner to limit the actual business impact of security incidents. Recurring analyses and defense processes are automated in order to react even more efficiently. Incidents are thoroughly investigated to derive additional measures to improve our overall security.
Business Continuity
Business continuity management is an integral component of the recognized ISO / IEC 27001 standard, primarily to ensure the availability of digital information processing facilities. Different Fresenius environments, such as our central IT infrastructure, as well as critical infrastructures in the medical sector, are ISO / IEC 27001-certified and regularly audited by independent auditors.
As part of the CARE programs, Fresenius has launched a group-wide initiative to identify, assess and protect all critical assets (i. e., CARE Critical Asset Protection). Insights of the assessments, specifically related to adverse impacts affecting the availability of critical assets, serve as input to the respective business continuity management.
Training
At Fresenius we seek to imbed a human-centered risk model, combining this with our already implemented Cybersecurity Training & Awareness Program (CTAP). The goal is to raise awareness and support a solid and mature cyber culture at Fresenius. The responsible team within the Cybersecurity Group function is called Culture & Training. Together with the respective Risk Domain Manager at segment-level, their activities are designed to enable our employees to build and improve their personal cybersecurity awareness, thus creating a line of defense against cyber-attacks. The Culture & Training team aims to share knowledge about emerging trends immediately, introducing different cybersecurity activities at Fresenius as well as providing helpful tips on the secure use of devices, be that in the office or at home.
In addition to mandatory training on cybersecurity fundamentals, CTAP offers various courses, videos, and other learning content, via the different digital CTAP learning platforms and intranets, for example. We regularly simulate phishing attacks to strengthen the required behavior to be triggered if phishing is suspected. We calculate a personal risk score for employees based on their behavior in phishing tests and the number of cybersecurity training sessions they have completed. All CTAP activities are tailored toward Fresenius’ specific risks and are available in several languages. The success of the CTAP activities is measured using predefined success criteria (e. g., the target phishing simulation click rate).
We inform our employees through various channels about current cyber risks and new types of cyber threats. The Culture & Training team further uses the knowledge derived from daily phishing attempts analyzed and evaluated in joint collaboration with the Cyber Emergency Response Team (CERT) to design new or updated training modules.
Reporting paths
If Fresenius employees suspect cyber threats, they can contact CERT@fresenius.com, CyberAware@fresenius.com, or any cybersecurity employee. To improve reporting efficiency, suspicious emails may be reported through the Phish Alert Button, which performs an automated analysis and involves the CERT, if required. Our CERT, together with the cyber defense segment teams, investigates possible threats and incidents in our IT, manufacturing, and healthcare facility environments, as well as suspected violations. If a malicious phishing attempt is detected, the sender is blocked and the security protocols are adapted accordingly.
Audits and monitoring
The Internal Audit departments carry out independent audits to improve the effectiveness of our risk management, internal control, and governance processes in all areas of the company. Cybersecurity aspects are taken into account in the risk-based annual planning and audit execution. The results of the audits are analyzed by the Cybersecurity Group function and are tracked and incorporated into the ongoing improvement of existing cybersecurity activities.
Furthermore, independent auditors conduct regular and comprehensive security assessments (e. g., penetration tests, security reviews of critical systems) and certification audits (e. g., ISO 27001, Health Data Hosting - HDS). Results from audits or other monitoring activities are evaluated if internal processes have to be adjusted. Additionally, we work with management consultancies and auditing companies to review and improve our cybersecurity processes. For security reasons, we cannot make any statements about specific review processes.
Our ambitions
It is our ambition that our patients and customers can always rely on the cybersecurity of our products and services. Hence, the objective of cybersecurity at Fresenius is to increase the maturity level of our cybersecurity capabilities, strengthen our resilience towards cyberattacks, and continuously mitigate our cyber risks. We evaluate the ever-changing threat landscape, define minimum security standards for our cyber risk domains, and implement appropriate security measures in a targeted, risk-based, and cost-effective manner through our cybersecurity program CARE. The members of the Cybersecurity Board annually develop targeted risk treatment plans with measures to safeguard the confidentiality, integrity, and availability of our digital information – and to continuously enhance the cybersecurity of our IT, manufacturing, and healthcare facility environments, as well as our medical devices.
Progress and measures in 2022
CARE Program
Throughout the reporting period, the various CARE sub-programs have been established to fulfil our ambition of increasing the maturity level of our cybersecurity capabilities, strengthening our resilience against cyberattacks, and constantly addressing our cyber risks. Selected progress in line with the CARE program structure is as follows:
Implementation of enhanced cybersecurity baseline measures, such as infrastructure/network hardening and standardization, secure remote access, e-mail security, application security, identity and access management controls.
Development of a tailored human risk model for different personas across the Fresenius workforce, further rollout of training and awareness solutions across the Group, various culture, training and awareness initiatives (e. g., CyberAware month).
Continued automatization of incident response processes, extension of external attack surface monitoring, monitoring of cyber risks posed by third-parties, formalized sharing of cyber threat intelligence internally and with external companies, setup of offensive security capability, launch of Group-wide training and testing of incident response procedures.
In-depth cybersecurity capability maturity assessment across the Group, further enhancement and rollout of metrics system, refinement of cybersecurity baseline, strategic threat intel analysis, regulatory requirements assessment, business-specific risk treatment plans, CARE program charter. Critical Assets: identification, assessment of business-critical assets, initiation and implementation of enhanced security measures.
Implementation of coordinated vulnerability disclosure process and integration in Fresenius website.
Planning and initiation of large-scale implementation projects for enhanced cybersecurity measures, such as segregation of manufacturing and IT environments.
Integration of cybersecurity into business continuity management and implementation of enhanced cybersecurity measures, such as monitoring of the healthcare facility networks.
Improvement through training
In the reporting year, training and awareness sessions, e. g., on new methods of phishing, have been conducted and several articles have been shared with the focus on increasing the fundamental cybersecurity knowledge. During the most recent CyberAware Month, which is organized every October, we have seen a rise and significant improvement in the level of engagement of our employees. The phishing tests conducted from 2020 to 2022 showed that the intensive training activities positively influenced our employees’ security awareness. After the level of difficulty was raised last year and the initial deterioration of the phishing rate, it has since been steadily improving thanks to further training sessions. There has also been a steady improvement in the reporting rate of phishing tests. We inform the respective employees individually and directly about the results in their personal dashboard. Further information is provided at Group level on our intranet.
Evaluation
We initiated and rolled out effectiveness metrics in accordance with the cybersecurity metrics system. According to this system, the objective of effectiveness metrics is to determine whether security controls are operating as intended and achieving their desired outcomes. This helps us in understanding cybersecurity risks and how well prepared or resilient we are against cyberattacks, by combining leading (e. g., average phishing simulation click rate) as well as trailing indicators (e. g., mean time required to resolve incidents). Rolled out metrics are collected across all the Group’s cybersecurity environments and are regularly reported to the Cybersecurity Board and CARE Steering Committee as well as visualized in a scorecard that allows cybersecurity management to steer cybersecurity efforts at Fresenius. The scorecard is shared with relevant stakeholders such as the Management and Supervisory Boards to enhance transparency regarding the overall cyber risk exposure and inform decision-making.
Overall, our resilience metrics indicate that we experienced only a few severe incidents during the reporting period. From a Group perspective these did not have a material impact on our business operations.
We abstain from reporting any cybersecurity specifics externally to avoid targeted attacks on our infrastructure.

