Ongoing digitization and digital transformation provide great opportunities for health care – with innovative, technological, and therapeutic approaches that improve the overall patient journey and treatment. Fresenius is entering these new markets with digital product solutions while acknowledging that digitization and digitalization are associated with cyber risks. We continuously strive to increase the security of our digital applications and systems to reduce cyber risks, and prevent harm to our patients or the company. All patients rely on us to ensure their safety and protect their health data.
Our approach
At the Fresenius Group, we pursue a holistic approach for the management of cybersecurity. We bring cybersecurity and business decision-makers in the Group together to develop a joint approach aligned with our strategic goals. We base our strategy on cyber-risk analyses and the security requirements of our four business segments. This approach is reflected in all Group security policies.
In 2017, the Management Board of Fresenius Management SE initiated the Cybersecurity Approach, Roadmap and Execution (CARE). Since 2018, CARE has represented the Group’s cybersecurity program, which bundles initiatives to strengthen our resilience in preventing and defending against cyber attacks. In 2020, the Management Board of Fresenius Management SE enacted a Group-wide Cybersecurity Policy that defines the objectives, structure, and operational organization for cybersecurity governance across the Fresenius Group, embedded in CARE.
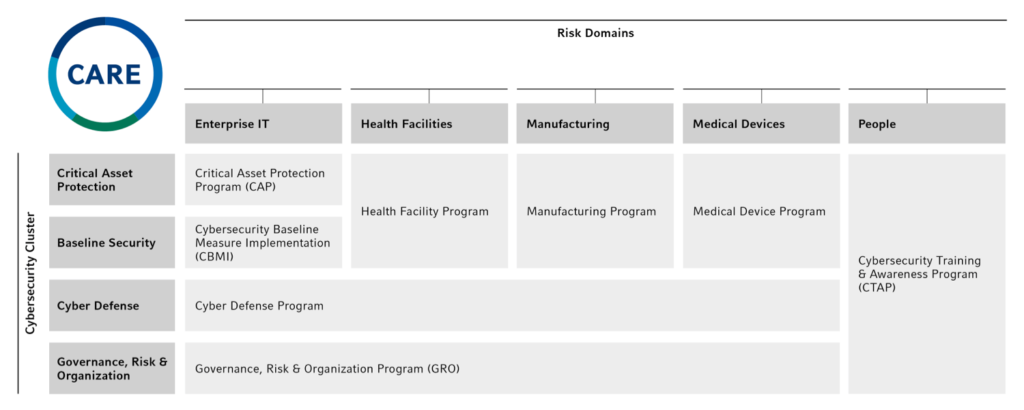
To manage Group-wide cybersecurity and associated risks, we have determined five risk domains. These are managed by the respective Risk Domain Managers – at corporate level and in the four business segments. Facilitated by the Group Cybersecurity Office (GCSO), the managers appoint Special Interest Groups (SIGs) that define cybersecurity requirements and coordinate risk management activities. The managers promote the use of best practices and the exchange of expertise and knowledge across all cybersecurity risk domains.
The five domains are:
- People: refers to the human factor of cybersecurity and includes all risks that could negatively affect the confidentiality, integrity, and availability of digital information due to inappropriate human behavior.
- Health Facilities: refers to cybersecurity in all health facilities such as hospitals, clinics, and treatment and rehabilitation centers. Related cyber risks include all risks that negatively affect the ability to serve patients.
- Medical Devices: refers to the cybersecurity of medical devices during their entire life cycle, from design to decommissioning. The risk domain includes all risks that could negatively affect the functionality and usability of medical devices.
- Enterprise IT: refers to cybersecurity in offices and administrative environments. This risk domain includes all risks that could negatively affect the ability of the cybersecurity of IT services to manage and process digital information.
- Manufacturing IT: refers to cybersecurity for production environments and associated facilities such as laboratories and warehouses. Related cybersecurity risks could negatively affect the performance and quality of production, including the ability to produce, label, and distribute products and meet compliance criteria.
The CARE program is structured along these risk domains across four cybersecurity clusters to ensure that our digital environment stays robust and recovers quickly in case of an incident. Overall, eight sub-programs have been set up to meet the primary objectives of the respective clusters in all risk domains:
- Critical Asset Protection: Protection for the most critical assets that are of highest value to the Group
- Baseline Security: Defining and implementing minimum cybersecurity standards
- Cyber Defense: Detecting and responding to cybersecurity incidents in a timely manner to limit the business impact
- Governance, and Risk & Organization: Establishing a foundation for effective cybersecurity governance
care program
The Opportunities and Risk Report contains further information on cybersecurity at Fresenius in 2021, in chapter Risk areas.
Certification and commitment
Cybersecurity insurance policies are in place at business segment level, where deemed suitable for risk transfer. In addition, there are certifications such as ISO / IEC 27001 at Group and business segment level. In addition, to complement the governance structure for risk minimization and to further hedge risks, the conclusion of a global cybersecurity insurance will continue to be evaluated at Group level.
Organization and responsibilities
The organizational structure
The CFO on the Fresenius Group Management Board oversees cybersecurity governance and receives direct reporting from the Group Head of Cybersecurity. The position of the Group Head of Cybersecurity, who acts as Group-wide Chief Information Security Officer (CISO), has overall responsibility for the governance of cybersecurity within the Fresenius Group and leads the Group Cybersecurity Office (GCSO). He defines the Group-wide cybersecurity strategy and coordinates this strategy with the respective cybersecurity heads in order to ensure an aligned approach across all business segments.
In the four business segments, the respective Business Segment Heads of Cybersecurity (Segment CISO) are responsible for the activities in the respective business segments. At Fresenius SE & Co. KGaA level, the Corporate Head of Cybersecurity is responsible for the individual corporate functions.
The GCSO enables and manages cybersecurity within the Fresenius Group. It ensures that relevant cybersecurity activities are organized and implemented at the business segment level, monitored, and coordinated from a Group perspective. Where necessary, the business segments are advised and supported in their activities.
cybersecurity organization
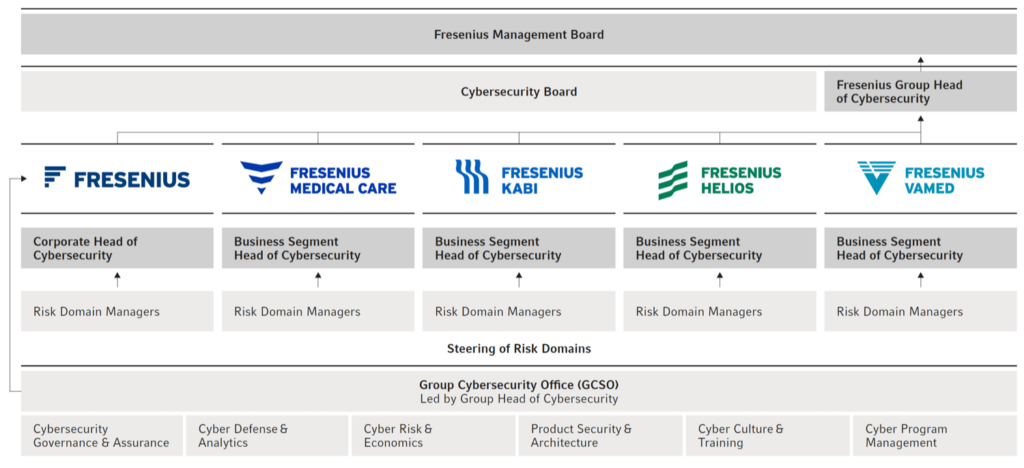
The GCSO is divided into six functions: Cyber Governance & Assurance, Cyber Risk & Economics, Products Security & Architecture, Cyber Defense & Analytics, Cyber Culture & Training, and Cyber Program Management.
The Cybersecurity Governance & Assurance function establishes and maintains a Group-wide Integrated Cybersecurity Management System (ICMS). Part of the ICMS is a framework for efficient management and regulation of cybersecurity within the Fresenius Group, as well as supporting processes to ensure the alignment of the cybersecurity strategy with the goals and objectives of the company in all risk domains.
The Cyber Risk & Economics function steers the identification, evaluation, and management of the Group’s strategic cyber risk exposure. By combining financial and economic know-how as well as standardized models to quantify and estimate future loss events, the function enables risk-based decision-making on effective cybersecurity investments and thereby continuously improves the Group’s level of security.
The Product Security & Architecture function is responsible for the development of the cybersecurity architecture and the risk domains Medical Devices, Manufacturing IT, and Health Facilities. The Medical Devices risk domain comprises all medical devices and products for which Fresenius has regulatory responsibility in accordance with applicable regulations and laws. The Manufacturing IT risk domain refers to all production, logistics, and associated facilities such as laboratories or warehouses. Within these facilities, it refers to all information technology/operational technology (IT/OT) equipment, systems, and processes, including all systems on which the production and delivery of Fresenius products depend. The Health Facilities risk domain refers to all health care facilities operated by Fresenius, such as hospitals, clinics, and other treatment and rehabilitation centers. Within these facilities, the risk domain refers to all IT/OT equipment and systems as well as processes and people relevant to the treatment of patients.
The Cyber Culture & Training function enables the cybersecurity teams of the four business segments to set up, run, and continuously improve their individual Cybersecurity Training & Awareness Programs (CTAP) to establish a cybersecurity culture at Fresenius. Through CTAP, we provide targeted training to our employees relevant to their roles and responsibilities, inform them about the latest cyber threats, and help them to recognize and protect themselves against cyber attacks in their everyday work.
The Cyber Program Management function steers the Group-wide cybersecurity program CARE. This includes Group-wide coordination and structuring, as well as monitoring and reporting of cybersecurity initiatives. The function also supports stakeholder management, particularly with regard to the cross-divisional Special Interest Groups (SIGs) and the Cybersecurity Board, to foster Group-wide collaboration.
At the operational level, the four business segments are responsible for their cybersecurity management. The business segments establish and report on strategic objectives and strategies for addressing risks. The objectives are based on the Group-wide cybersecurity strategy and are autonomously defined by the Business Segment Heads of Cybersecurity, who are responsible for implementation.
In addition, the cross-divisional Cybersecurity Board meets on a bi-monthly basis. It consists of the Group Head of Cybersecurity, the Corporate Head of Cybersecurity, and all Business Segment Heads of Cybersecurity. It ensures the exchange of information on Group-wide cybersecurity matters between the business segments and Group functions, defines criteria for evaluating and monitoring the development of cybersecurity across the Group, and reviews the progress and results of cybersecurity measures and initiatives. The Cybersecurity Board also monitors the adoption and implementation of the Group-wide cybersecurity policies.
The individuals responsible for cybersecurity usually have many years of experience in cybersecurity management, extensive knowledge, and appropriate professional certifications.
The reporting structures
The CFO of the Fresenius Group, as a member of the Management Board of Fresenius Management SE, is informed about cybersecurity-related topics on a weekly basis by the Group Head of Cybersecurity, and as required. The Group Head of Cybersecurity reports quarterly to the Management Board of Fresenius Management SE and at least annually to the Supervisory Board. The Chief Financial Officers of the business segments, and for Fresenius Vamed the member of the Management Board responsible for the service business, meet on a quarterly basis in the CARE Steering Committee to organize regular reporting and to steer the cybersecurity initiatives across the business segments.
The Business Segment Heads of Cybersecurity inform the respective members of the CARE Steering Committee and additionally report on cybersecurity matters to their Management Boards at least on a bi-annual basis. The Risk Domain Managers report to their respective Heads of Cybersecurity. In addition, the Data Protection, Enterprise Risk Management, and Compliance departments regularly exchange information on matters relating to cybersecurity.
Guidelines and regulations
Cybersecurity policy framework
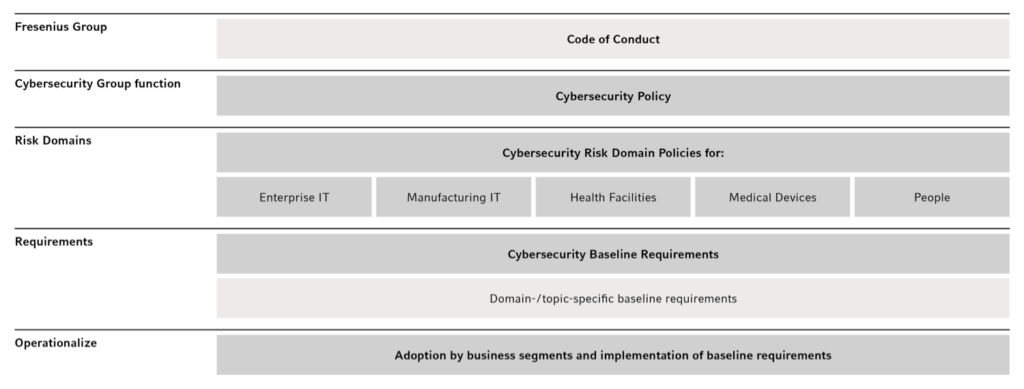
Our Cybersecurity Policy Framework consists of a set of policies, requirements, and procedures. It forms the foundation for cybersecurity in all business segments and Group functions. Within this framework, we define confidentiality, integrity, and availability as our key objectives for protecting digital information, technologies, and systems across our risk domains. It was approved by the Management Board of Fresenius Management SE and the management committees of the four business segments.
The Cybersecurity Policy is based on the Fresenius Code of Conduct and follows internationally recognized standards and best practices, such as the Charter of Trust. It defines the overarching policy and organizational structure for cybersecurity governance in the Fresenius Group. The underlying Risk Domain Policies specify the framework, processes, and roles and responsibilities for each risk domain to attain the overarching objectives of protecting the confidentiality, integrity, and availability of Fresenius’ digital information in a holistic manner.
- Enterprise IT:
- Scope: all corporate IT at Fresenius, extending to all IT services and products that manage and/or process digital information of Fresenius’ offices and administrative environments
- Manufacturing IT:
- Scope: all manufacturing environments including production, logistics, and associated facilities such as laboratories and warehouses; within these facilities all IT/OT devices, systems, processes, and persons in accordance with International Society of Automation (ISA) Levels 0 to 3
- Medical Devices:
- Scope: all medical devices that Fresenius manufactures or sells under the Fresenius or a Fresenius-owned brand name
- Health Facilities:
- Scope: all hospitals and clinics as well as treatment and rehabilitation centers owned by Fresenius; within these facilities: all IT/OT devices, systems, processes, and people relevant to patient care
- People:
- Scope: all entities of Fresenius and their respective employees, temporary workers, and volunteers
The four business segments also have specific minimum security standards, which take into account specific regulatory requirements or local legislation. Minimum security standards already established in the four business segments are leveraged as Group-wide standards where appropriate.
Our ambitions
The objective of our cybersecurity program CARE, which covers all risk domains, is to increase the maturity level of our cybersecurity capabilities, strengthen our resilience towards cyber attacks, and continuously reduce our cyber risks. We evaluate the ever-changing threat landscape, define minimum security standards for our cyber risk domains, and implement appropriate security measures in a targeted, risk-based, and cost-effective manner. The Cybersecurity Board annually develops Group-wide and business-unit-specific operational objectives and measures to safeguard the confidentiality, integrity, and availability of our digital information – and to continuously enhance the cybersecurity of our IT, manufacturing, and health facility environments ,as well as our medical devices. These are coordinated via the Group Head of Cybersecurity and are submitted to the CARE Steering Committee, which is established at Management Board level and meets on a quarterly basis.
Progress and measures in 2021
CARE Program
Throughout the reporting period, the various CARE sub-programs have been established to fulfil our ambition of increasing the maturity level of our cybersecurity capabilities, strengthening our resilience against cyber attacks, and constantly addressing our cyber risks. Selected progress in line with the CARE program structure is outlined below:
- Cybersecurity Baseline Measure Implementation (CBMI): implementation of enhanced cybersecurity baseline measures, such as endpoint detection and response (EDR) solutions, strengthened authentication mechanisms for critical areas
- Cyber Training & Awareness (CTAP): extending the reach of the Group-wide training and awareness platform; conducting various training and phishing campaigns; establishing the cybersecurity awareness brand (“Cyber Aware”) and associated materials such as posters, videos, and merchandise articles
- Cyber Defense: aligning incident response procedures; implementing the “Fresenius Virtual Cyber Defense Center” and the “Fresenius Intelligence Office”; extending monitoring visibility to enable early detection and fast response
- Governance, Risk & Organization: implementing a cybersecurity governance structure; assessing cybersecurity capability maturities; defining a cybersecurity risk management framework; conducting several cyber risk insurance dialogs to evaluate cyber risk transfer
Risk analysis
In accordance with the newly established Group-wide Cybersecurity Risk Management Framework, the GCSO – together with the business segments – conducts a business-driven evaluation of the strategic cybersecurity risks along Fresenius’ value chains. The cyber risks of the Group are attributed to the business activities of the respective business segments. While the cyber risks in the product business are closely related to interruptions to manufacturing or logistic processes, as well as theft of intellectual property, the risks in our health care facilities are related to patients, their health information, and the medical devices used. We continuously derive our cybersecurity measures from the bi-annual cyber risk evaluations in order to effectively mitigate our risks.
We are currently in the process of designing a cybersecurity metrics system that will enhance transparency regarding the overall cyber risk situation of Fresenius. To this end, we defined an initial set of metrics (e. g., what we refer to as crown jewels with critical weak points, average phishing simulation click rate, mean time required to resolve incidents), which in future are to be collected across all the Group’s cybersecurity environments. This will help us to understand how well prepared and resilient we are to prevent (stay robust) and recover (recover quickly) from a cyber attack. In the next step, the system design will be gradually rolled out to complement the existing cybersecurity governance structure.
Our Risk Report contains extensive information on the effects of cyber risks on risk management; see chapter Risk areas of our Annual Report 2021.
Security concept
To protect the Group’s value generation, we have developed tailored frameworks for our five cybersecurity risk domains that define the security architectures, concepts, and requirements. We have been implementing the frameworks successively since 2021. The respective preventive, detective and corrective measures are prioritized and implemented through our CARE program to effectively reduce risk. While our main objective is to prevent cyber risks from materializing, we can detect cyber threats at an early stage through various monitoring solutions in order to respond in a timely manner and limit the actual business impact of security incidents. Recurring analyses and defense processes are automated in order to react even more efficiently. Incidents are thoroughly investigated to derive additional measures to improve our overall security.
Training
In 2019, we launched the Cybersecurity Training & Awareness Program (CTAP). The goal is to establish a cyber culture at Fresenius, enabling our employees to learn about cybersecurity risks and how to deal with them, and to develop the habits to protect themselves against cyber attacks. In addition to mandatory training on data protection and information security, CTAP offers various courses, games, videos, and other cybersecurity learning content, such as the digital CTAP learning platform. We regularly simulate phishing attacks to monitor the effectiveness of the training and to provide users with information on an appropriate response if phishing is suspected. We calculate a personal risk score for employees based on their behavior in phishing tests and the number of cybersecurity training sessions they have completed. All CTAP activities are tailored toward Fresenius’ specific risks and are available in several languages. The success of the CTAP activities is measured using predefined success criteria.
In addition, we constantly inform our employees through various channels about current cyber risks and new types of cyber threats. We also organize a Cybersecurity Awareness Month in October each year. In October 2021, various webinars were conducted, with a focus on the cyber threats posed by the still high number of employees working from home. Further, webinars for employees’ children were offered as “cyber junior training”. We are convinced that children and young teenagers have a comparably high need for cyber awareness, especially in view of the increased use of remote learning during the COVID-19 pandemic.
The phishing tests conducted in 2020 and 2021 showed that the intensive training activities positively influenced our employees' security awareness. Therefore, the level of difficulty was raised. The phishing rate initially deteriorated and improved again in the course of the year, thanks to further training sessions. We inform the respective employees individually and directly about the results in their personal dashboard. Further information is provided at Group level on our intranet.
Reporting paths
If Fresenius employees suspect cyber threats, they can contact CERT@fresenius.com, CyberAware@fresenius.com, or any cybersecurity employee. To improve reporting efficiency, suspicious mails may be reported through the “Phish Alert Button”, which performs an automated analysis and involves the Cyber Emergency Response Team (CERT), if required. Our CERT investigates possible threats and incidents in our IT, manufacturing, and health facility environments, as well as suspected violations. If a malicious phishing attempt is detected, the sender is blocked and the security protocols adapted accordingly.
Evaluation
We established our Fresenius Group cybersecurity governance structure in 2020 and further improved it in 2021: part of the further development and improvement of our cybersecurity governance is the definition and reporting of KPIs, e. g., the total number of breaches, along with substantiated classification by severity. We are diligently working to further mature our KPI reporting system for the Fresenius Group. In the meantime, we abstain from reporting any KPIs externally, either in total or by risk domain. The increase in reporting transparency must always be in compliance with our risk prevention activities. Information from our external reporting must not lead to targeted attacks on our infrastructure.
Audits and monitoring
The Internal Audit departments carry out independent audits to improve the effectiveness of our risk management, internal control, and governance processes in all areas of the company. Cybersecurity aspects are taken into account in the risked-based annual planning and audit execution. The results of the audits are analyzed by the Cybersecurity Group function and are incorporated into the ongoing improvement of existing cybersecurity activities.
Furthermore, independent auditors conduct regular and comprehensive security assessments (e.g., penetration tests, security reviews of critical systems) and certification audits (e.g., ISO 27001, HDS). Results from audits or other monitoring activities are evaluated if internal processes have to be adjusted. Additionally, we work with management consultancies and auditing companies to review and improve our cybersecurity processes. For security reasons, we cannot make any statements about specific review processes.

